Proxy vs VPN
Understanding the Differences
Learn the key differences between proxy and VPN services, including technical protocols, security levels, and use cases. Understand why some protocols are easily blocked while others remain undetectable.
What is the difference between a Proxy and a VPN?
While both of these technologies will keep you anonymous by hiding your IP address, they work in slightly different ways. A proxy acts as a gateway to the software you use it in, for example your ISP is your gateway to the internet, same idea for the proxy to your software, proxys (apart from SSH proxys) are not encrypted but traffic wont reach your network to begin with. An anonymous VPN will protect your entire internet connection the moment you connect to it, disguising your use of everything from utorrent to email to basic web browsing by establishing a virtual network via our servers to reroute all your traffic and DNS.
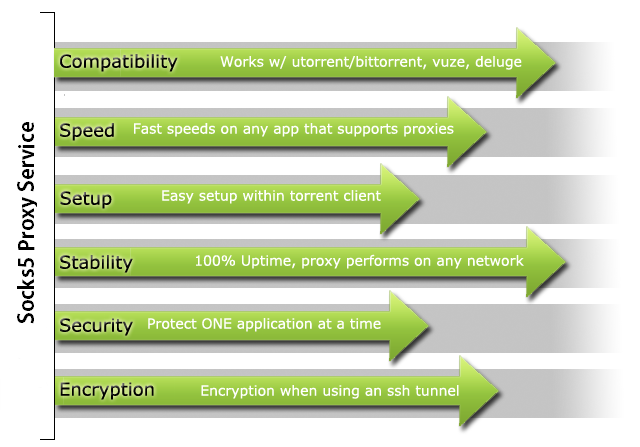
Proxy Service:
Think of a proxy server as a gateway. You have control over proxy settings, which only affect your torrent client (utorrent, bittorrent, vuze, ect) or any other program that supports socks5 proxies. A proxy only provides IP masking to one application at a time. When you download and seed torrents or browse the web, all your traffic is routed through the anonymous proxy server and directly to you. This means that peers in the torrent swarm will not see your IP address, but rather the IP address of TorGuard's proxy server. When using a torrent proxy, you get all the benefits of torrenting and the proxy server, including security, speed, geographic location, and an anonymous IP.
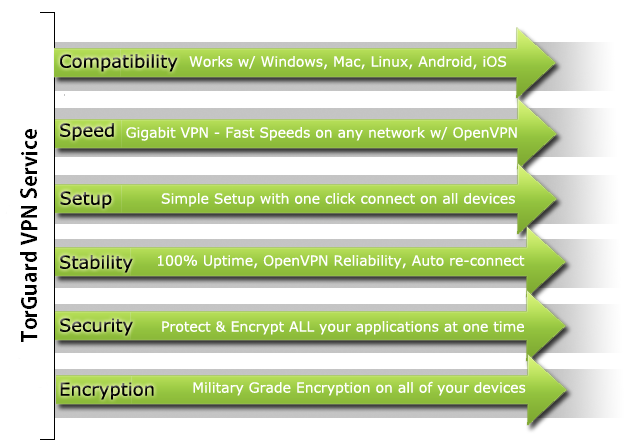
VPN Service:
Unlike a proxy, which only secures your torrent client or web browser, VPN (Virtual Private Network) encrypted tunneling secures 100% of all your internet access, replacing your local ISP routing for all applications. With a fully anonymous VPN server, you will enjoy enhanced security regardless of geographic location. This protects not only your torrent downloads but also all other online activity or programs such as your web browser, email, and any other third party applications that connect to the web. You'll also get faster connections and military grade encryption when using a VPN like TorGuard. And, your VPN can easily be connected or disconnected with just one mouse click.
Technical Protocol Comparison
Understanding the Technology Behind Proxies and VPNs
SOCKS5 Proxy Protocol
SOCKS5 is a proxy protocol that operates at Layer 5 (Session Layer) of the OSI model. It's application-specific and doesn't encrypt traffic by default.
Best for: Best for torrenting, gaming, and specific application routing where speed is priority over encryption.
VPN Protocols (OpenVPN/WireGuard)
VPN protocols operate at Layer 3 (Network Layer) and create encrypted tunnels for all device traffic. They provide system-wide protection.
Best for: Best for complete privacy, security, and when accessing sensitive information or bypassing censorship.
Why VPN Protocols Get Blocked
Modern firewalls and DPI (Deep Packet Inspection) systems can easily identify and block traditional VPN protocols due to their distinctive patterns and behaviors.
VPN Protocol Signatures
V2Ray Protocol Advantages
V2Ray vs Traditional VPN Protocols
Next-Generation Proxy Technology
V2Ray represents the evolution of proxy technology, designed specifically to bypass sophisticated censorship and traffic analysis systems.
| Aspect | V2Ray | Traditional VPN | Winner |
|---|---|---|---|
| Detectability | Virtually undetectable - mimics normal web traffic | Easily detected by DPI and traffic analysis | V2RAY |
| Blocking Resistance | Extremely difficult to block without breaking normal internet | Can be blocked by protocol signatures and ports | V2RAY |
| Setup Complexity | More complex configuration and setup required | Simple one-click connection and setup | VPN |
| Speed | Good speed with optimized configurations | Generally faster due to optimized protocols | VPN |
| Device Support | Limited native support, requires specific clients | Universal support across all devices and platforms | VPN |
| Censorship Bypassing | Excellent at bypassing even sophisticated censorship | Limited effectiveness against advanced censorship | V2RAY |
Which Should You Choose?
Making the Right Decision for Your Needs
Choose VPN When:
Choose SOCKS5 Proxy When:
Choose V2Ray When:
Ready to choose the right solution for your needs?