⚡ About WireGuard
WireGuard is an extremely simple yet fast and modern VPN protocol that utilizes state-of-the-art cryptography. It's designed to be faster, simpler, leaner, and more useful than IPsec while avoiding complexity. Particularly beneficial for routers with limited CPU power.
Why WireGuard on DD-WRT?
✨ WireGuard Benefits
- Ultra-Fast Performance: Up to 4x faster than OpenVPN on routers
- Low CPU Usage: Perfect for consumer routers with limited processing power
- Modern Cryptography: ChaCha20, Curve25519, BLAKE2s, SipHash24
- Minimal Attack Surface: Only ~4,000 lines of code vs OpenVPN's ~100,000
- Quick Reconnection: Seamless roaming between networks
- Lower Latency: Ideal for gaming and real-time applications
Performance Comparison
Protocol Comparison
WireGuard
- ✅ Fastest performance
- ✅ Lowest latency
- ✅ Minimal CPU usage
- ✅ Modern crypto only
- ✅ Built into kernel
- ❌ No obfuscation
OpenVPN
- ✅ Most compatible
- ✅ Obfuscation options
- ✅ Mature & stable
- ❌ Higher CPU usage
- ❌ Slower on routers
- ❌ Complex setup
IPSec/L2TP
- ✅ Native support
- ✅ Good compatibility
- ❌ Outdated crypto
- ❌ Can be blocked
- ❌ Setup complexity
- ❌ Performance issues
DD-WRT Requirements
⚠️ Important Requirements
- DD-WRT Version: Must have WireGuard support (build r44048 or newer)
- Router CPU: ARM or newer MIPS processors recommended
- RAM: 128MB minimum, 256MB+ recommended
- Kernel: Must support WireGuard kernel module
Note: Not all DD-WRT builds include WireGuard. Check your build's feature list.
Step-by-Step Configuration
Access Router Interface
Navigate to your DD-WRT router's web interface:
- Default:
192.168.1.1 - Alternative:
192.168.0.1
Log in with your administrator credentials.
Create WireGuard Tunnel
Navigate to Setup → Tunnels:
- Click Add Tunnel button
- Select Enable
- Choose WireGuard from the dropdown menu
- Click Save
🔑 Key Generation
After saving, DD-WRT will display:
- Private Key: Keep this secret!
- Public Key: You'll need this for TorGuard config
Click Generate Key if keys aren't shown, then copy both keys.
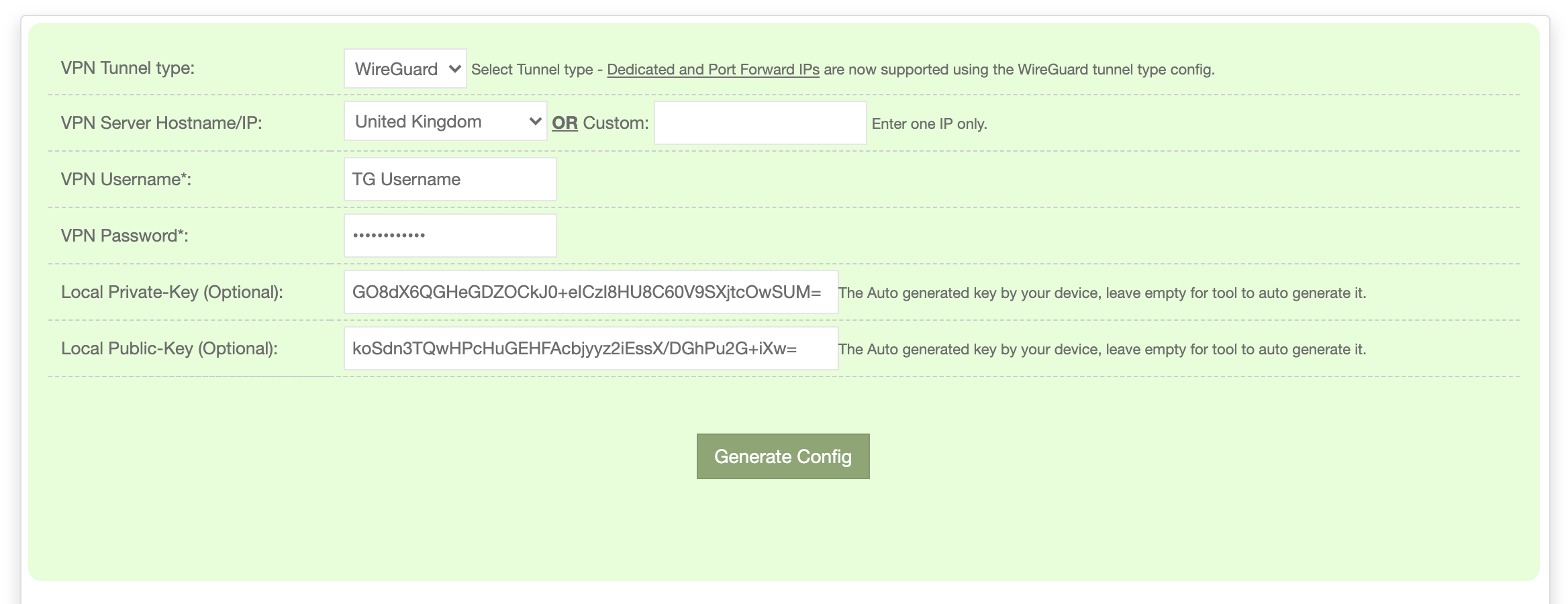
Generate TorGuard Config
Visit the TorGuard Config Generator:
Configuration Steps:
- VPN Tunnel type: Select "WireGuard"
- Server Location: Choose your preferred server or enter Dedicated IP
- VPN Username: Enter your TorGuard username
- Local Public-Key: Paste the public key from DD-WRT
- Local Private-Key: Paste the private key from DD-WRT
- Click Generate Config
Configure DD-WRT Settings
Using your generated config, fill in the DD-WRT tunnel settings:
Enable
Enable
[Server IP from config]:1443
📍 Allowed IPs Configuration
Set to: 0.0.0.0/1, 128.0.0.0/1
This routes all internet traffic through the VPN while maintaining local network access.
Enable
25
[From generated config]
Add Peer Configuration:
[Address from config, e.g., 10.x.x.x]
255.255.255.255
Click Save after entering all settings.
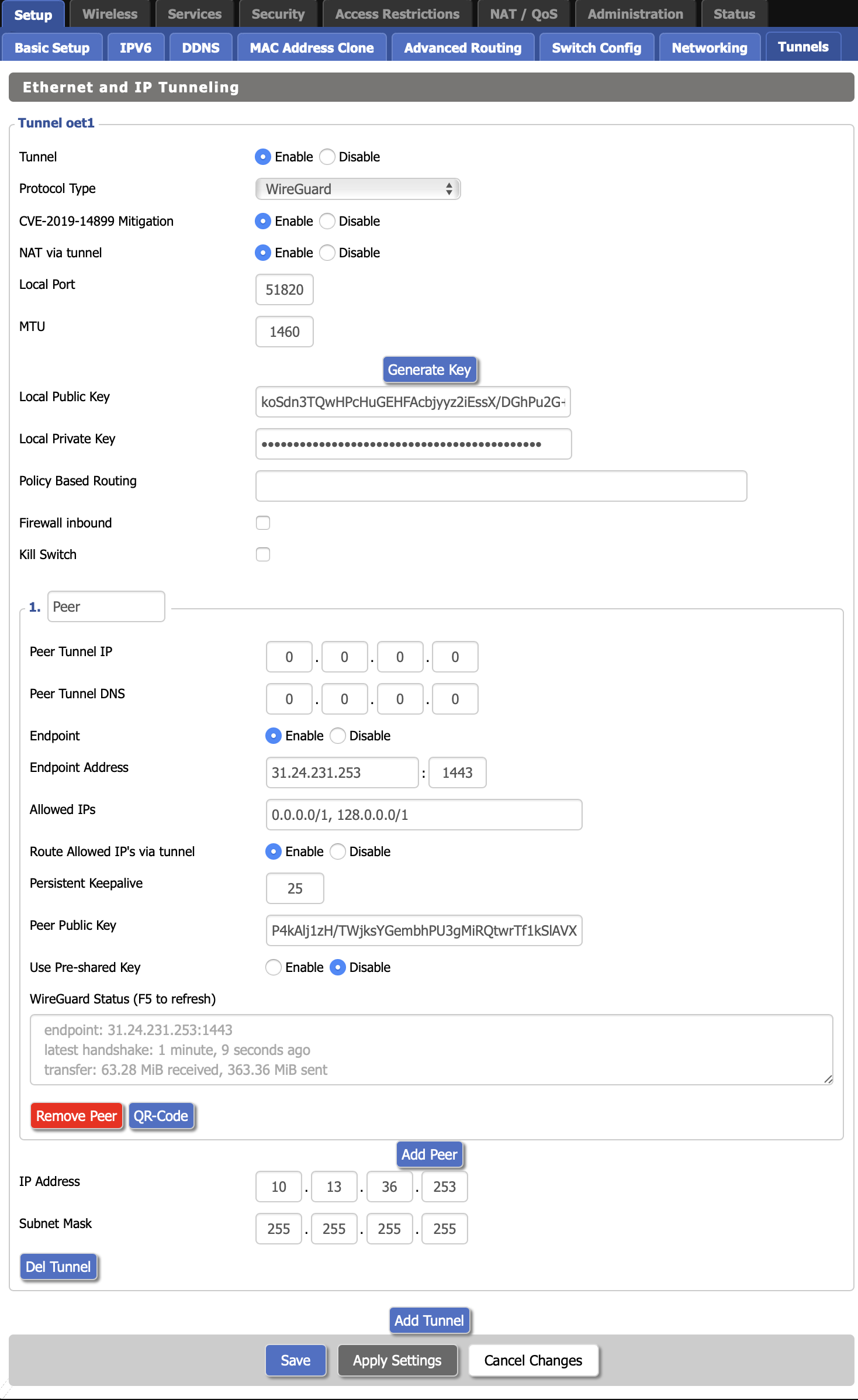
Finally, click Apply Settings to activate the tunnel.
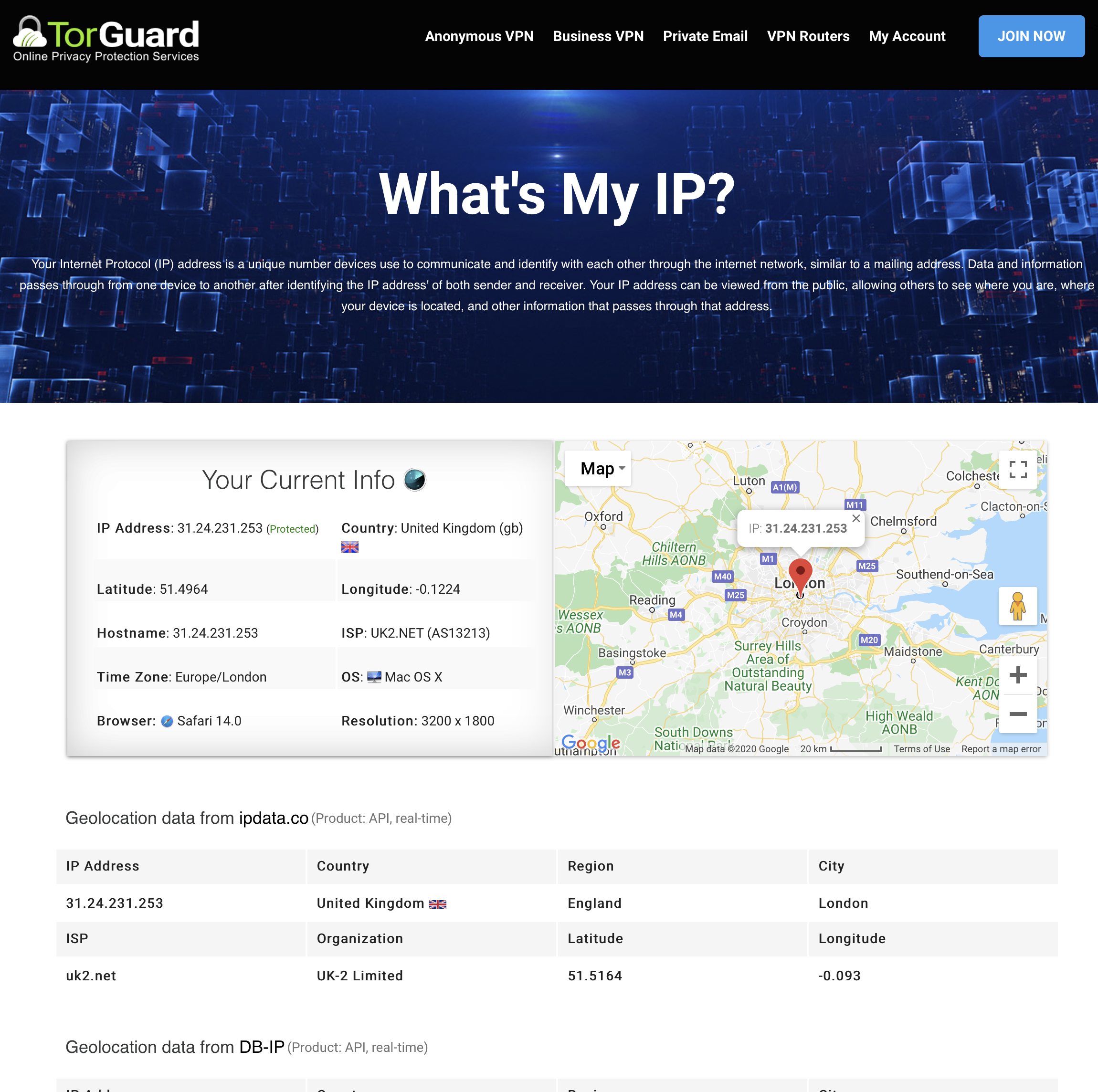
Verify Connection
Connect a device to your DD-WRT router's network and verify:
- Browse to TorGuard IP Check
- Confirm IP shows TorGuard server location
- Verify status shows "Protected"
WireGuard Cryptography
🔐 Security Specifications
- Key Exchange: Curve25519 for ECDH
- Encryption: ChaCha20 stream cipher
- Authentication: Poly1305 authenticator
- Hashing: BLAKE2s hash function
- Hashtable keys: SipHash24
- Perfect Forward Secrecy: Yes, every 2 minutes
All cryptographic choices are fixed - no downgrade attacks possible!
Feature Comparison
| Feature | WireGuard | OpenVPN |
|---|---|---|
| Code Size | ~4,000 lines | ~100,000 lines |
| Setup Time | <100ms | 2-8 seconds |
| Handshake | 1-RTT | Multi-RTT |
| Crypto Agility | No (fixed, modern) | Yes (configurable) |
| Roaming | Seamless | Reconnect required |
| CPU Usage | Very Low | Moderate-High |
Router Compatibility
✅ Known Compatible Models
Note: Requires DD-WRT build with WireGuard support. Older/weaker routers may not support WireGuard.
Advanced Configuration
🔧 Advanced Options
MTU Optimization
For better performance, you can set MTU in Additional Config:
MTU = 1420
DNS Configuration
To use TorGuard DNS servers:
- Go to Setup → Basic Setup
- Set Static DNS 1:
10.8.0.1 - Set Static DNS 2:
10.9.0.1
Kill Switch
To block internet if VPN disconnects:
- Administration → Commands
- Add firewall rules to block WAN access
- Only allow traffic through wg0 interface
Troubleshooting
No Connection
- Verify endpoint IP and port (1443)
- Check keys match config exactly
- Ensure WireGuard module is loaded
- Try regenerating config
Slow Speeds
- Check router CPU usage
- Try different server location
- Verify MTU settings
- Update DD-WRT firmware
DNS Issues
- Set static DNS servers
- Clear DNS cache
- Check allowed IPs includes DNS
- Disable IPv6 if problematic
Security Considerations
🔒 Security Best Practices
- Key Security: Never share your private key
- Regular Updates: Keep DD-WRT firmware updated
- Firewall Rules: Configure proper firewall rules
- DNS Leak Protection: Use TorGuard DNS servers
- IPv6: Disable if not routed through VPN
Performance Tips
💡 Optimization Tips
- Server Selection: Choose geographically close servers
- Router Placement: Ensure good ventilation for CPU cooling
- QoS Settings: Configure Quality of Service for priority traffic
- Channel Selection: Use less congested Wi-Fi channels
- Hardware Acceleration: Enable if your router supports it
Need Help?
If you're experiencing issues with WireGuard on DD-WRT:
Include your DD-WRT build number and router model
Additional Resources: