PPTP Security Timeline
1999
First PPTP vulnerabilities discovered
2012
Moxie Marlinspike breaks MS-CHAPv2
2016
Microsoft removes PPTP from Windows 10
2025
Still using PPTP? You're 26 years behind!
About Mikrotik RouterOS
Mikrotik routers are professional-grade networking equipment used in enterprise environments. Using PPTP on these routers puts your entire network at risk and may violate corporate security policies.
Secure Alternatives for Mikrotik
✅ WireGuard (Recommended)
- Modern, fast, secure
- Supported in RouterOS 7+
- Minimal CPU usage
- Perfect for site-to-site
✅ IKEv2/IPSec
- Enterprise standard
- Hardware acceleration
- Native RouterOS support
- FIPS compliant
✅ OpenVPN
- Widely supported
- Highly configurable
- Good security
- Community packages available
⚖️ Legal & Compliance Issues
Using PPTP may violate:
- GDPR: Insufficient protection of personal data
- HIPAA: Does not meet encryption standards
- PCI-DSS: Fails security requirements
- SOC 2: Inadequate security controls
- Corporate Policies: Most companies prohibit PPTP
If You MUST Use PPTP (Test Environment Only)
The following instructions are provided solely for isolated test environments. DO NOT use in production.
1Access Mikrotik Router
- WebFig: http://[router-ip]
- Winbox: Download from mikrotik.com
- SSH: ssh admin@[router-ip]
2Create PPTP Interface
Navigate to Interfaces → Add New → PPTP Client

Configure:
- Name: TorGuard-PPTP
- Connect To: [server-ip]
- User: Your TorGuard username
- Password: Your TorGuard password
- Uncheck: "Add Default Route"
3Configure Firewall NAT
IP → Firewall → NAT → Add New

- Chain: srcnat
- Out Interface: TorGuard-PPTP
- Action: masquerade
4Create Mangle Rules
For selective routing - IP → Firewall → Mangle → Add New
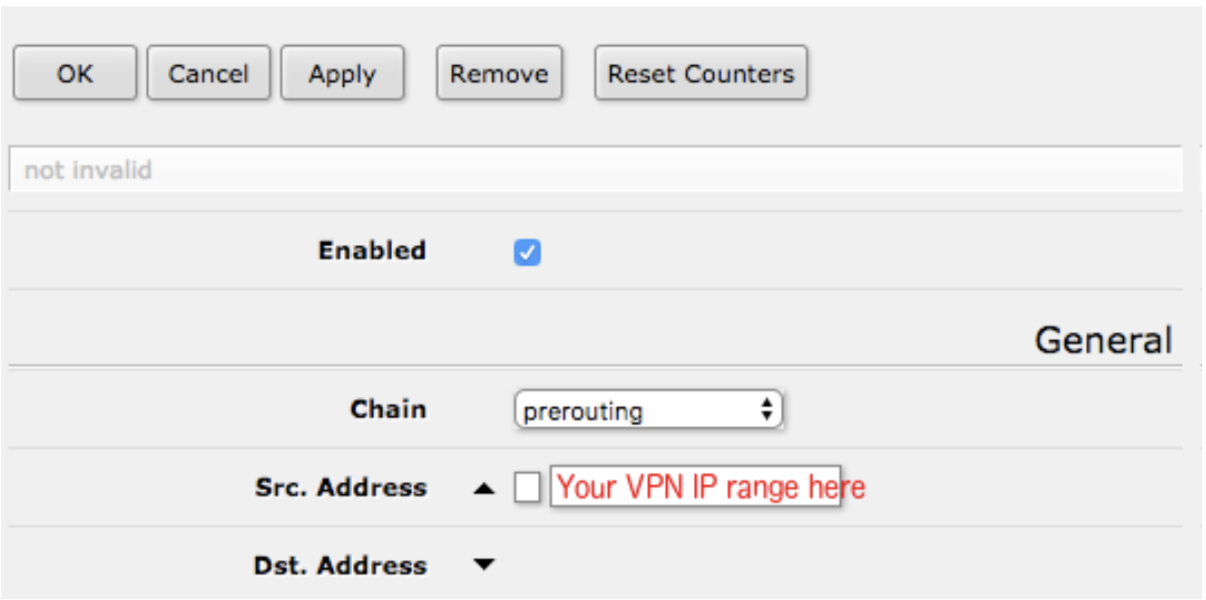
- Chain: prerouting
- Src Address: Device IPs to route through VPN
- Action: mark routing
- New Routing Mark: VPN
5Add Route
IP → Routes → Add New
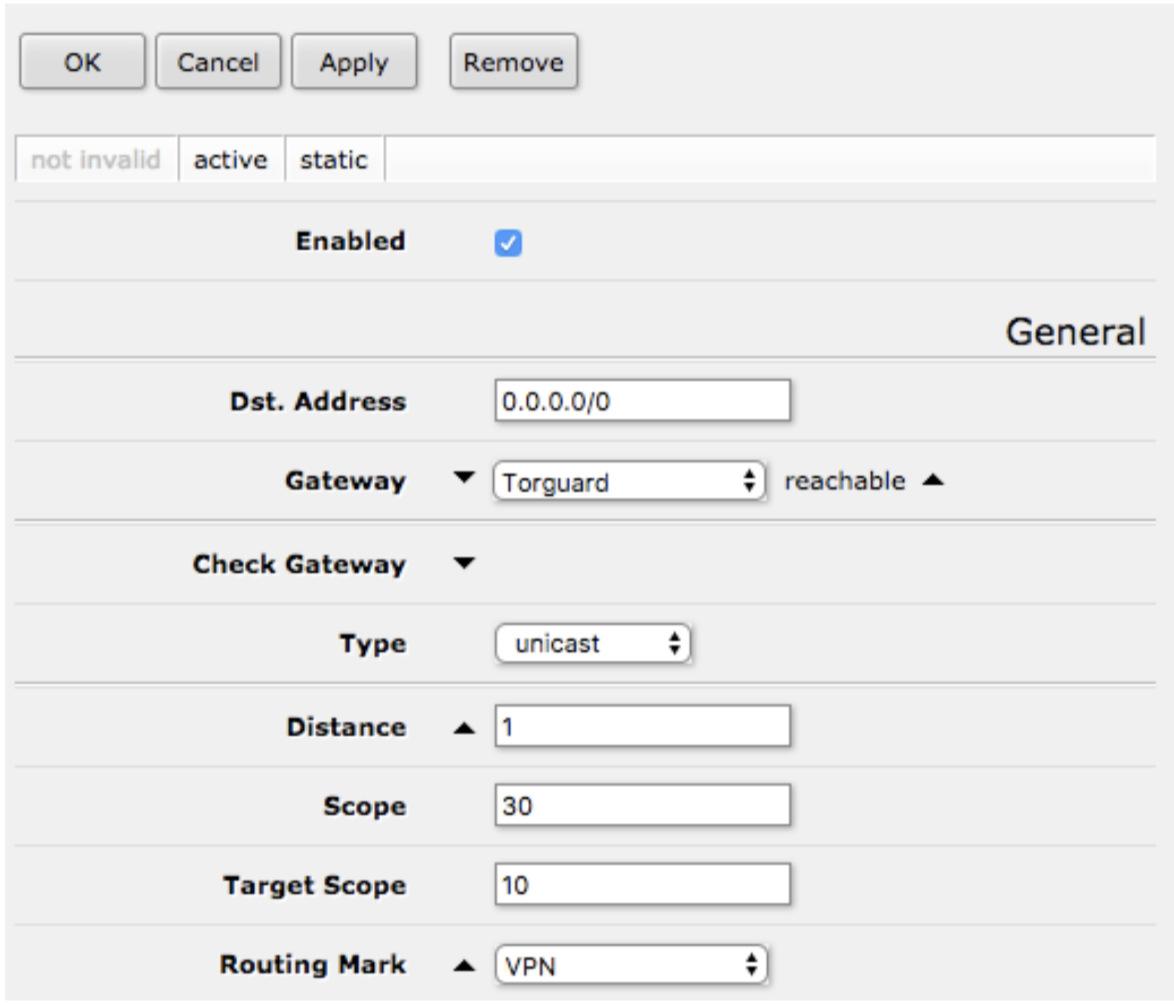
- Dst Address: 0.0.0.0/0
- Gateway: TorGuard-PPTP
- Routing Mark: VPN
Migration to Secure Protocols
🔄 Migration Steps
-
Audit Current Usage
- Document which devices use PPTP
- Identify bandwidth requirements
- Note any special routing needs
-
Choose Replacement Protocol
- WireGuard: Best for RouterOS 7+
- IKEv2: Best for compatibility
- OpenVPN: Most flexible
-
Test New Configuration
- Set up parallel to PPTP
- Test with non-critical devices
- Verify performance meets needs
-
Migrate Gradually
- Move devices one by one
- Monitor for issues
- Keep PPTP as fallback temporarily
-
Decommission PPTP
- Disable PPTP interface
- Remove firewall rules
- Document new setup
Mikrotik VPN Protocol Comparison
| Protocol | Security | Speed | CPU Usage | RouterOS Support |
|---|---|---|---|---|
| PPTP | ❌ BROKEN | Fast | Low | All versions |
| L2TP/IPSec | ⚠️ Moderate | Moderate | Medium | All versions |
| IKEv2/IPSec | ✅ Excellent | Fast | Medium | v6.45+ |
| OpenVPN | ✅ Excellent | Moderate | High | Package required |
| WireGuard | ✅ Excellent | Fastest | Lowest | v7.0+ |
Common Mikrotik Commands
Useful commands for troubleshooting (via SSH/Terminal):
# Check interface status /interface print # View active connections /interface pptp-client monitor 0 # Check routes /ip route print # View firewall NAT rules /ip firewall nat print # Disable PPTP (recommended) /interface pptp-client disable 0 # Remove PPTP interface /interface pptp-client remove 0
Professional Recommendations
✅ What You Should Do
- Use WireGuard on RouterOS 7.x
- Implement IKEv2 for older RouterOS
- Consider hardware upgrade if needed
- Enable firewall logging for audit trails
- Use certificate-based authentication
- Implement proper network segmentation
Emergency Support
If you're currently using PPTP in production and need help migrating:
Our team can help you quickly migrate to a secure protocol