🛡️ About Stealth Proxy
TorGuard's Stealth Proxy uses advanced obfuscation techniques to disguise VPN traffic as regular HTTPS traffic, bypassing even the most sophisticated VPN detection and blocking systems. Essential for restrictive networks and censored regions.
Why Use Stealth Proxy?
Stealth Proxy is your ultimate solution when standard VPN connections are blocked or throttled. It wraps your VPN traffic in an additional layer of encryption that appears as normal web traffic to firewalls and deep packet inspection systems.
Critical Use Cases
🇨🇳 Censored Countries
Bypass government firewalls in:
- China (Great Firewall)
- Iran
- UAE
- Russia
- Turkey
🏢 Corporate Networks
Access blocked content at:
- Offices with strict policies
- Hotels with restrictions
- Conference centers
- Public institutions
🎓 Educational Networks
Bypass restrictions at:
- Universities
- Schools
- Libraries
- Research facilities
📡 ISP Throttling
Prevent detection by:
- ISPs throttling VPNs
- Mobile carriers
- Public WiFi filters
- Network administrators
How Stealth Proxy Works
🔬 Technical Details
Traffic Obfuscation
Disguises OpenVPN packets as regular HTTPS traffic using stunnel or obfsproxy
Protocol Masking
Removes VPN signatures and patterns that DPI systems look for
Port 443 Usage
Uses the same port as HTTPS websites, making blocking difficult
Double Encryption
VPN encryption wrapped in SSL/TLS layer for maximum security
VPN Detection Methods
🔍 What Stealth Proxy Bypasses
Deep Packet Inspection
Analyzes packet headers and payload patterns
Port Blocking
Blocks common VPN ports (1194, 1723, etc.)
Protocol Detection
Identifies OpenVPN/WireGuard signatures
Traffic Analysis
Detects VPN-like traffic patterns
Step-by-Step Setup
Access Settings
Click the settings cog icon in the top-right corner of the TorGuard desktop application:

Enable Stealth Proxy
Navigate to the Proxy tab and configure:
- Check the "Stealth Proxy" checkbox
- Select a Stealth Proxy location (choose closest for best speed)
- Click Save
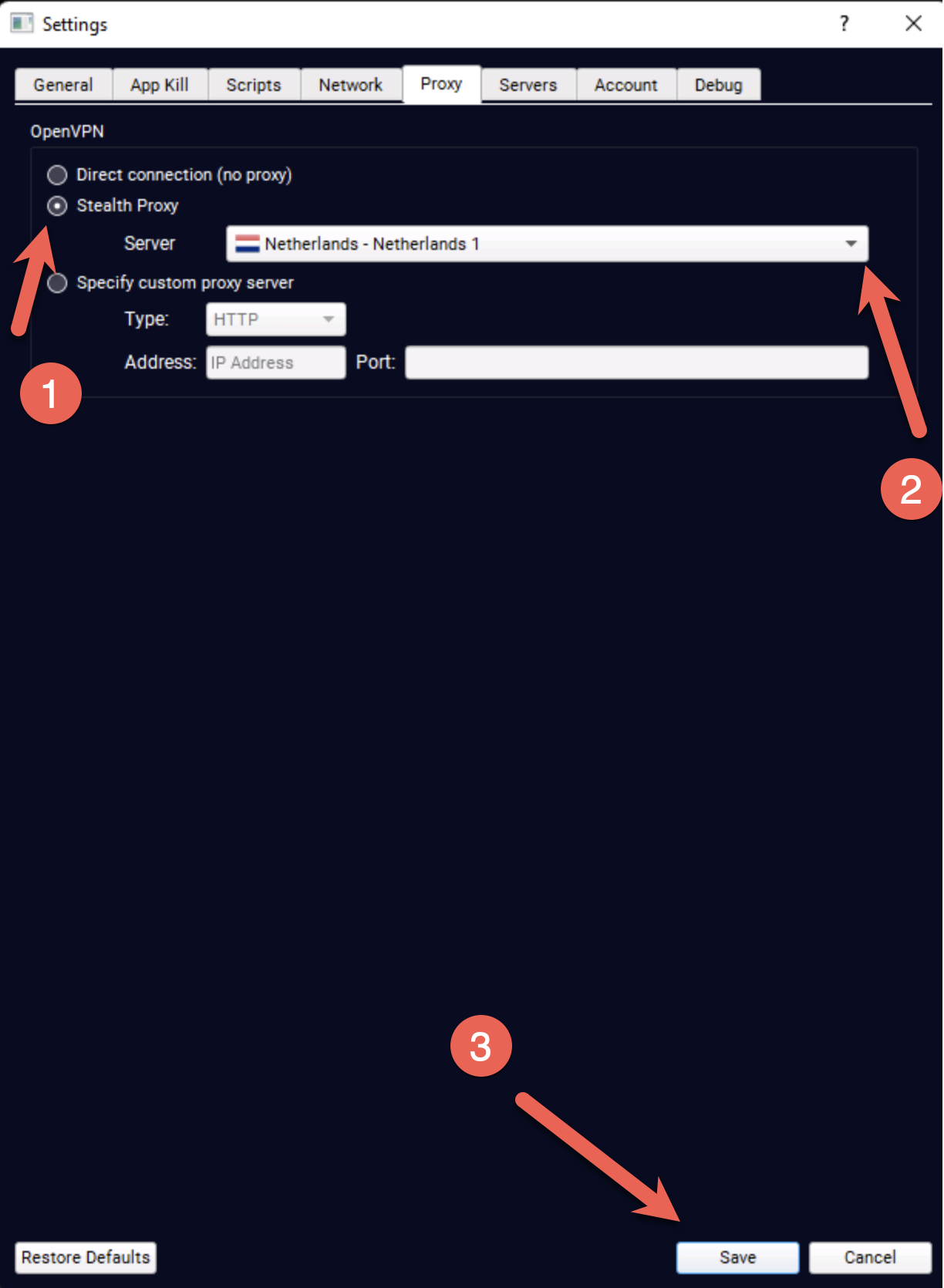
💡 Location Selection
Choose a stealth proxy server geographically close to you for optimal performance. The proxy adds an extra hop, so proximity matters.
Open Connection Settings
Return to the main screen and click the hamburger menu (☰) in the top-left corner:

Configure Connection
Ensure proper settings for stealth connection:
- Tunnel Type: Must be set to OpenVPN (Stealth doesn't work with WireGuard)
- Port: Try different ports if blocked (see recommendations below)
- Protocol: TCP usually works better than UDP for stealth
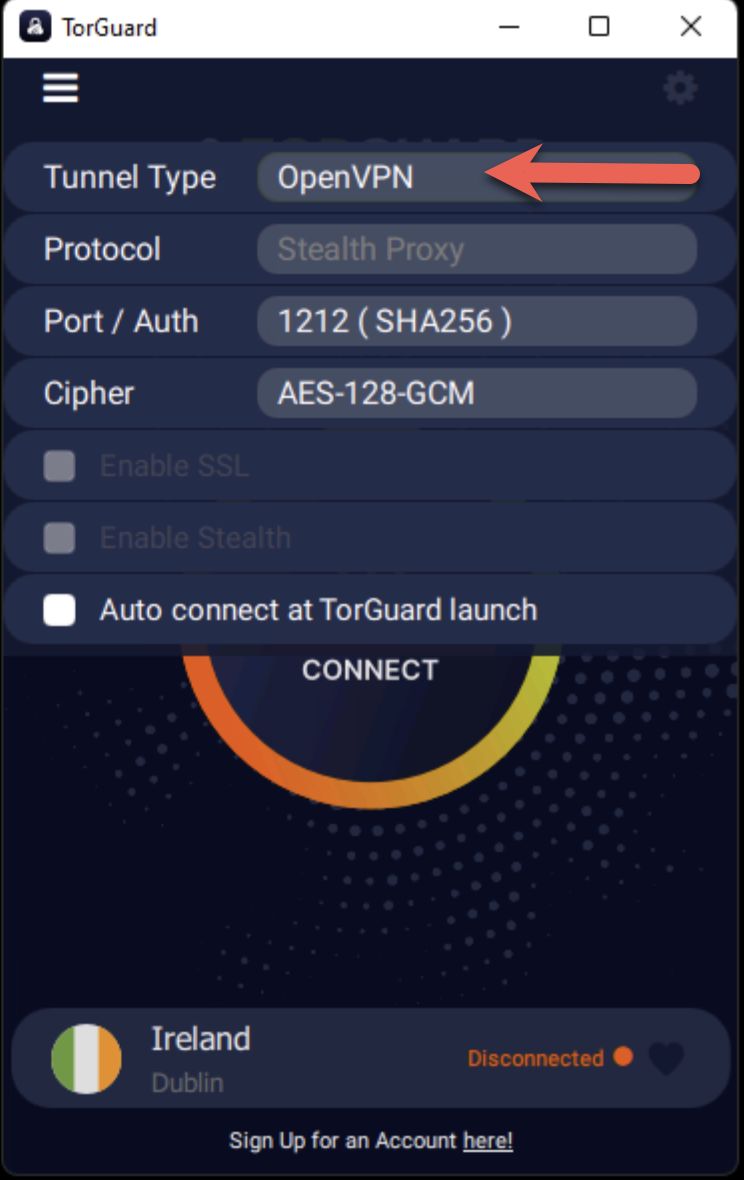
Connect to VPN
Click connect to establish your stealth VPN connection.
⚠️ Connection Display
When connected via stealth proxy, the app shows the VPN server IP instead of "verified". This is normal behavior when using stealth mode.
Recommended Port Configuration
🔌 Best Ports for Stealth
Port 443
HTTPS (Best)
Rarely blockedPort 80
HTTP
Usually openPort 995
POP3S
Email portPort 993
IMAPS
Email portPort 465
SMTPS
Email portPort 22
SSH
If allowedPro Tip: Cycle through different ports to find what works best in your location. Start with 443, then try 80, then email ports.
Performance Impact
📊 Speed Considerations
Stealth Proxy adds an extra encryption layer, which impacts performance:
Speed reduction
Added latency
CPU usage
For access!
Note: Only use Stealth when regular VPN is blocked. The performance trade-off is worth it for bypassing censorship.
Comparison Table
| Feature | Regular VPN | Stealth Proxy VPN |
|---|---|---|
| Speed | Fastest | 20-40% slower |
| Detection Resistance | Low | Very High |
| DPI Bypass | No | Yes |
| Port Options | Many | Limited (443 best) |
| Protocol Support | All | OpenVPN only |
| CPU Usage | Normal | Higher |
| Best Use Case | General privacy | Censorship bypass |
Troubleshooting
🔧 Common Issues & Solutions
Connection Failed
- Try different stealth server
- Change port to 443 or 80
- Use TCP instead of UDP
- Check firewall settings
Very Slow Speed
- Choose closer stealth server
- Reduce encryption to AES-128
- Try different VPN server
- Check ISP throttling
Still Blocked
- Ensure OpenVPN selected
- Try port 443 TCP
- Change stealth location
- Contact support
Drops Frequently
- Enable persistent connection
- Increase timeout values
- Use wired connection
- Check proxy server load
DNS Leaks
- Enable DNS leak protection
- Use TorGuard DNS
- Check at ipleak.net
- Disable IPv6
Authentication Error
- Verify credentials
- Check subscription status
- Try different server
- Re-login to app
Alternative Methods
🔄 If Stealth Proxy Fails
Shadowsocks
Alternative obfuscation protocol designed for censorship bypass
SSH Tunnel
Use SSH to tunnel VPN traffic through port 22
Bridge Servers
Connect through intermediate servers in unrestricted countries
V2Ray
Advanced protocol with multiple obfuscation methods
Security Considerations
⚠️ Important Security Notes
- Performance Trade-off: Extra encryption layer reduces speed but increases security
- Traffic Analysis: While encrypted, traffic patterns might still be analyzed
- Server Trust: You're trusting the stealth proxy server as an additional hop
- Legal Implications: Check local laws regarding VPN usage and circumvention
- Activity Logging: Ensure TorGuard's no-logs policy covers stealth servers
Best Practices
✅ Stealth Proxy Tips
- Use When Needed: Only enable for restrictive networks
- Port Selection: Start with 443, then try alternatives
- Server Proximity: Choose geographically close servers
- Regular Testing: Test connection before important use
- Backup Methods: Have alternative bypass methods ready
- Stay Updated: Keep TorGuard client updated for latest features
Need Help?
If you're having trouble with Stealth Proxy or need assistance bypassing restrictions:
Specify your location, network type, and what blocking you're experiencing