DD-WRT transforms consumer routers into powerful VPN gateways, protecting your entire network with a single configuration. This comprehensive guide covers OpenVPN setup on DD-WRT builds from 2015 through 2025, including advanced features like kill switches, policy-based routing, and performance optimization.
🌐 Benefits of Router-Level VPN
- Whole Network: All devices protected automatically
- Device Limit Bypass: Unlimited devices on one connection
- Smart Home: VPN for IoT devices without apps
- Gaming Consoles: Xbox, PlayStation, Switch protection
- Always On: No need to connect each device
DD-WRT Router Compatibility
| Router Model | CPU Speed | RAM | VPN Speed | Recommended |
|---|---|---|---|---|
| Netgear R7000 | 1 GHz | 256 MB | 25-35 Mbps | ⭐⭐⭐⭐ |
| Asus RT-AC68U | 800 MHz | 256 MB | 20-30 Mbps | ⭐⭐⭐⭐ |
| Linksys WRT3200ACM | 1.8 GHz | 512 MB | 50-70 Mbps | ⭐⭐⭐⭐⭐ |
| Netgear R9000 | 1.7 GHz | 1 GB | 70-100 Mbps | ⭐⭐⭐⭐⭐ |
Prerequisites
- DD-WRT Version: Build 25000 or newer (2015+)
- Router: Compatible model with 8MB+ flash
- TorGuard Account: Active VPN subscription
- Credentials: VPN username/password (not email)
- Time: 15-30 minutes for setup
Step 1: Access DD-WRT Interface
- Open web browser and navigate to router IP:
- Default:
192.168.1.1 - Alternative:
192.168.0.1
- Default:
- Login with DD-WRT credentials
- If first setup, change default password
Step 2: Enable OpenVPN Daemon
Navigate to Services → VPN tab:
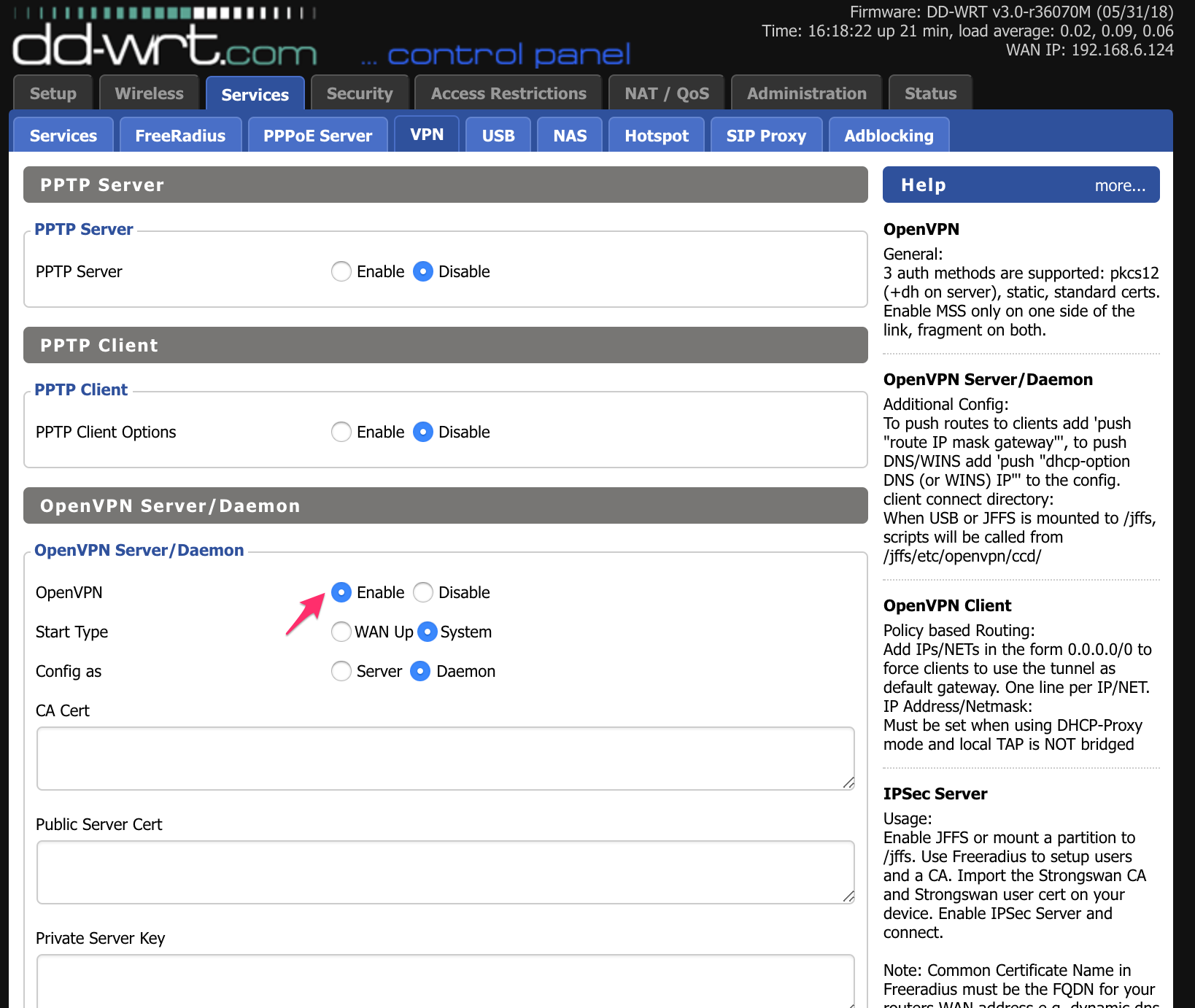
Enable OpenVPN Server/Daemon - this provides logging even when using client mode.
Step 3: Configure OpenVPN Client
Scroll down and Enable OpenVPN Client:
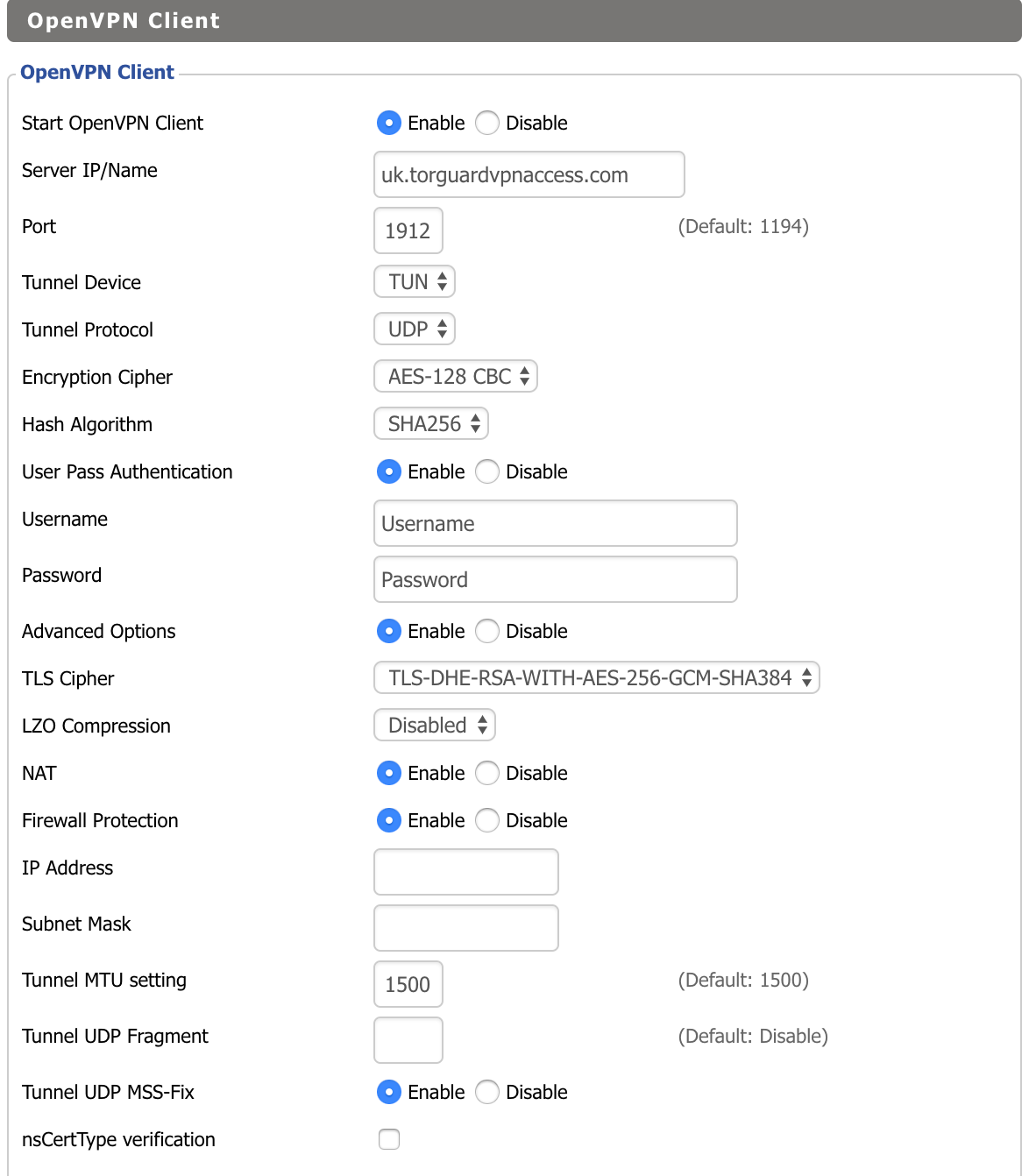
Basic Configuration
| Setting | Value | Notes |
|---|---|---|
| Server IP/Name | ny.east.usa.torguardvpnaccess.com | View all servers |
| Port | 1912 | Or 443, 1194, 1195 (specs) |
| Tunnel Device | TUN | Layer 3 tunnel |
| Tunnel Protocol | UDP | Faster than TCP |
| Encryption Cipher | AES-128-CBC | Good balance |
| Hash Algorithm | SHA256 | Check port specs |
Authentication
- User Pass Authentication: Enable
- Username: Your TorGuard VPN username
- Password: Your TorGuard VPN password
Advanced Options
- Advanced Options: Enable
- TLS Cipher: TLS-DHE-RSA-WITH-AES-256-GCM-SHA384
- LZO Compression: Disabled
- NAT: Enable
- Firewall Protection: Enable
- Tunnel UDP MSS-Fix: Enable
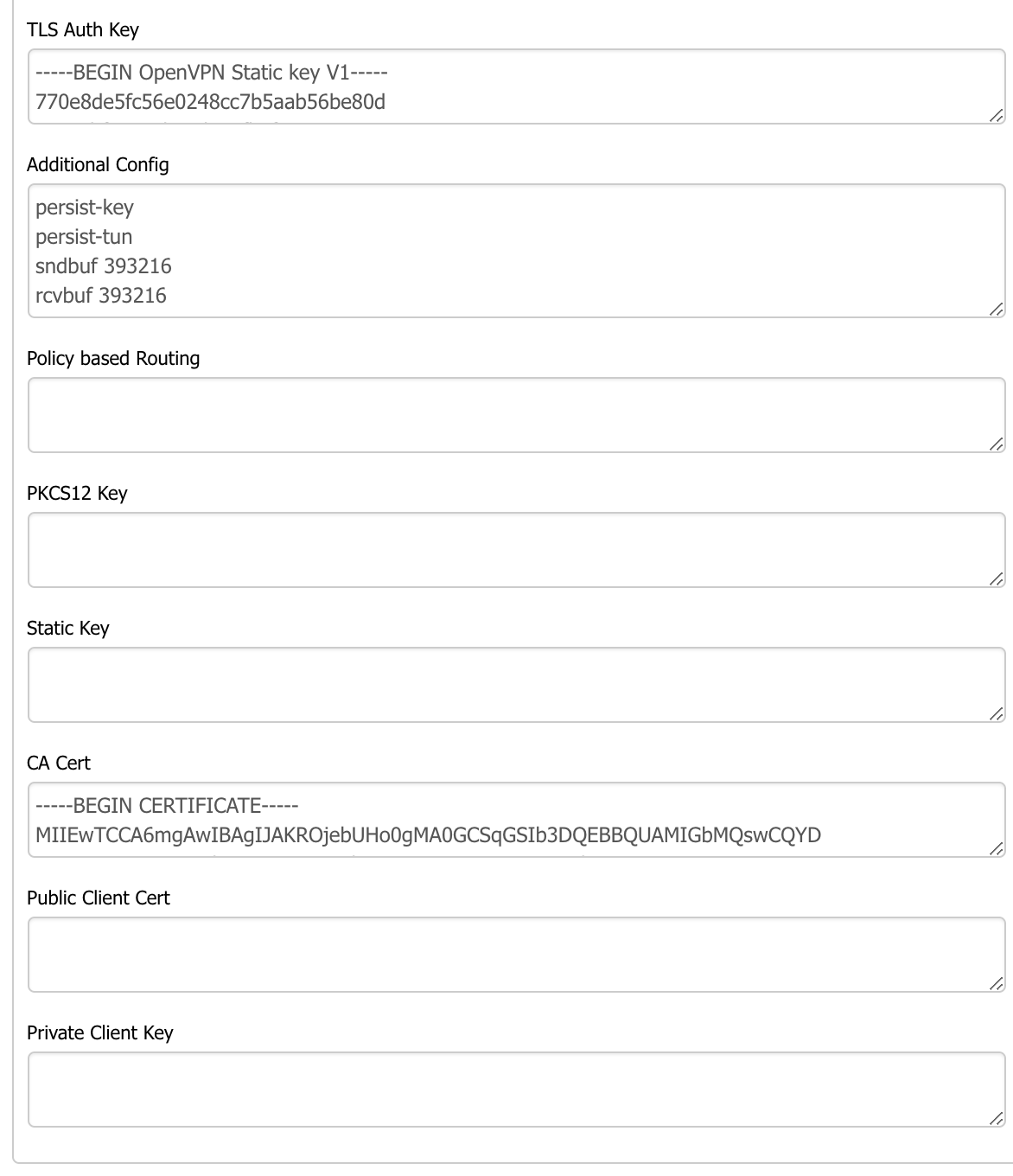
Step 4: Additional Configuration
In the Additional Config box, add:
persist-key
persist-tun
sndbuf 393216
rcvbuf 393216
remote-cert-tls server
verify-x509-name server name
key-direction 1
tls-version-min 1.2Certificates
- Visit TorGuard certificates page
- Copy TLS-AUTH Key → paste in TLS Auth Key box
- Copy OpenVPN CA → paste in CA Cert box
Step 5: Save and Reboot
- Click Save at bottom of page
- Click Apply Settings
- Go to Administration → Management
- Scroll down and click Reboot Router
- Wait 3-5 minutes for full restart
Verify VPN Connection
Method 1: Check IP Address
- Visit TorGuard IP Check
- Verify IP shows VPN location
Method 2: OpenVPN Status
- Go to Status → OpenVPN
- Check for "CONNECTED SUCCESS" message
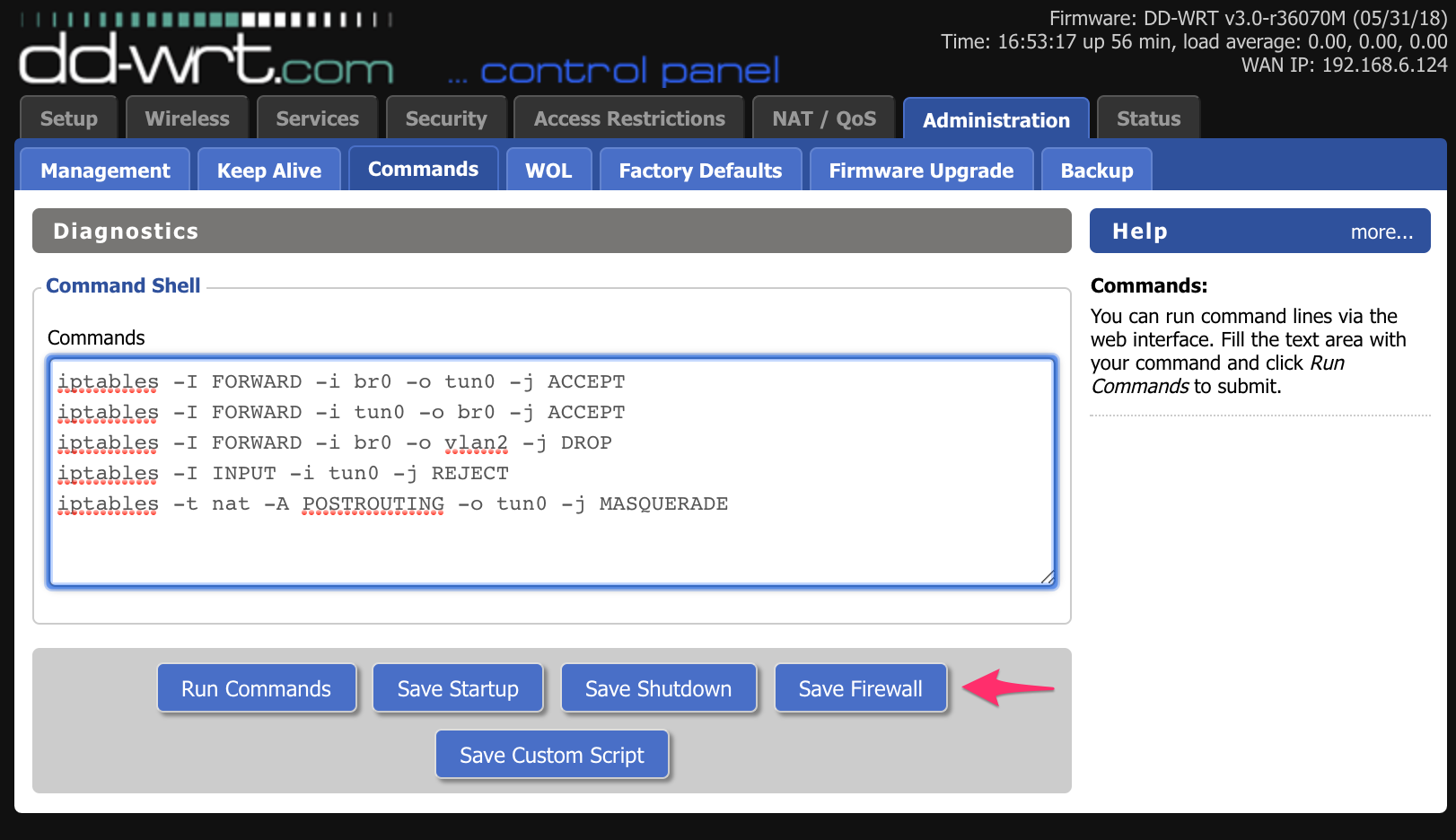
Kill Switch Configuration
Prevent IP leaks if VPN disconnects:
- Go to Administration → Commands
- Enter these firewall rules:
iptables -I FORWARD -i br0 -o tun0 -j ACCEPT
iptables -I FORWARD -i tun0 -o br0 -j ACCEPT
iptables -I FORWARD -i br0 -o vlan2 -j DROP
iptables -I INPUT -i tun0 -j REJECT
iptables -t nat -A POSTROUTING -o tun0 -j MASQUERADE- Click Save Firewall
ifconfig command while VPN is running.
Policy-Based Routing
Route only specific devices through VPN:
Step 1: Modify Additional Config
Add to Additional Config box:
route-nopullStep 2: Configure Device IPs
In Policy Based Routing field, enter device IPs:

Example format:
192.168.1.100/32
192.168.1.101/32
192.168.1.150/32Performance Optimization
1. CPU Overclocking (Advanced)
# Check current CPU speed
cat /proc/cpuinfo
# Overclock (example - varies by model)
nvram set clkfreq=1200,800
nvram commit
reboot2. Optimize Cipher
- Fastest: AES-128-CBC
- Balanced: AES-128-GCM
- Secure: AES-256-GCM
3. Buffer Tuning
# Add to Additional Config
sndbuf 524288
rcvbuf 524288
tun-mtu 1500
mssfix 1450Troubleshooting Guide
Connection Failures
| Issue | Solution |
|---|---|
| Wrong credentials | Use VPN username, not email |
| Time sync error | Enable NTP client, set timezone |
| DNS issues | Try DNSMasq settings variations |
| IP conflicts | Change router to 192.168.1.x subnet |
| MTU problems | Add: tun-mtu 1100 |
Enable Logging
Add to Additional Config:
verb 3
log /tmp/openvpn.logView logs:
# SSH into router, then:
cat /tmp/openvpn.log
# Or create web-accessible log:
ln -s /tmp/openvpn.log /tmp/www/openvpnlog.html
# Access at: http://192.168.1.1/user/openvpnlog.htmlCommon Error Messages
- AUTH_FAILED: Wrong username/password
- TLS Error: Certificate mismatch or outdated
- Connection Timeout: Port blocked or server down
- Route Addition Failed: IP conflict with local network
Advanced Features
Multiple VPN Profiles
Switch between servers via script:
#!/bin/sh
# Save as /jffs/scripts/vpn-switch.sh
stopservice openvpn
nvram set openvpncl_remoteip="$1"
nvram commit
startservice openvpnAutomatic Reconnection
Add to Additional Config:
resolv-retry infinite
connect-retry 5 30
keepalive 10 60DNS Leak Prevention
# Force DNS through VPN
dhcp-option DNS 10.8.0.1
block-outside-dnsAlternative Firmware Comparison
| Feature | DD-WRT | OpenWRT | Tomato | Merlin |
|---|---|---|---|---|
| OpenVPN GUI | ✅ | ✅ | ✅ | ✅ |
| WireGuard | Limited | ✅ | ❌ | ✅ |
| Ease of Use | ⭐⭐⭐⭐ | ⭐⭐⭐ | ⭐⭐⭐⭐⭐ | ⭐⭐⭐⭐ |
| Performance | ⭐⭐⭐⭐ | ⭐⭐⭐⭐⭐ | ⭐⭐⭐⭐ | ⭐⭐⭐⭐ |
✅ Setup Complete Checklist
- OpenVPN client enabled and configured
- Certificates and keys properly pasted
- Kill switch firewall rules saved
- Router rebooted after configuration
- VPN connection verified via IP check
- DNS leak test passed
Need DD-WRT Help?
Our support team specializes in router VPN configurations and can help troubleshoot DD-WRT issues or recommend optimal settings for your network.
Get Router Support