QNAP NAS devices support multiple VPN protocols for secure remote access and privacy protection. While this guide covers PPTP for legacy compatibility, we strongly recommend using OpenVPN or WireGuard for modern security. VPN on your NAS enables secure remote file access, protects downloads, and can share VPN connection with your entire network.
⚠️ PPTP Security Warning
PPTP is obsolete and insecure! It can be cracked in minutes and provides no real security. We include PPTP instructions only for legacy device compatibility.
- ❌ Broken encryption (MS-CHAPv2 compromised)
- ❌ Vulnerable to NSA/government surveillance
- ❌ Easy to block by ISPs
- ✅ Use OpenVPN or WireGuard instead
VPN Protocol Comparison for QNAP
| Protocol | Security | Speed | CPU Usage | Recommendation |
|---|---|---|---|---|
| WireGuard | ⭐⭐⭐⭐⭐ | ⭐⭐⭐⭐⭐ | Low | Best choice |
| OpenVPN | ⭐⭐⭐⭐⭐ | ⭐⭐⭐⭐ | Medium | Recommended |
| L2TP/IPsec | ⭐⭐⭐⭐ | ⭐⭐⭐ | Medium | Acceptable |
| PPTP | ⭐ | ⭐⭐⭐⭐⭐ | Low | ❌ Avoid |
QNAP Model Compatibility
| QNAP Series | OpenVPN | WireGuard | Max Speed |
|---|---|---|---|
| TS-x53 Series | ✅ | ✅ (QPKG) | 50-100 Mbps |
| TS-x73 Series | ✅ | ✅ (QPKG) | 100-200 Mbps |
| TVS-x72 Series | ✅ | ✅ | 200-500 Mbps |
| TS-hx86 Series | ✅ | ✅ | 500+ Mbps |
Recommended: OpenVPN Setup (Secure)
Step 1: Download OpenVPN Config
- Login to TorGuard client area
- Go to Tools → OpenVPN Config Generator
- Select server location
- Download .ovpn config file
Step 2: QNAP OpenVPN Configuration
- Open Control Panel → VPN Client
- Click Add → Select OpenVPN
- Import the .ovpn file
- Enter credentials:
- Username: Your VPN username
- Password: Your VPN password
- Enable Use default gateway on remote network
- Enable Reconnect when VPN connection is lost
Legacy: PPTP Setup (Not Recommended)
Step 1: Access VPN Client Settings
Open the Control Panel and click VPN Client:
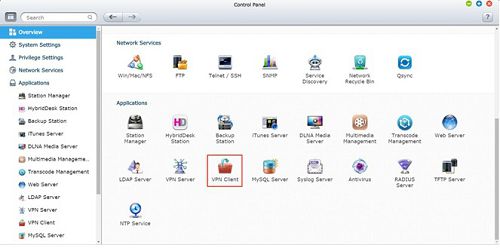
Step 2: Add PPTP Profile
Click Add, then choose PPTP in the dropdown menu:

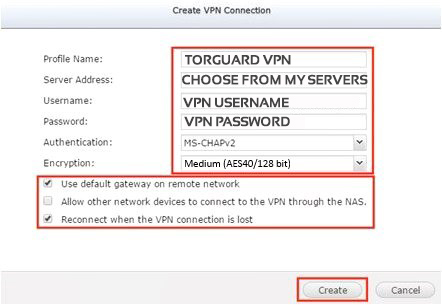
Step 3: Configure PPTP Settings
Enter the following configuration:
- Profile Name: TorGuard VPN (or location-specific like "TorGuard UK")
- Server address: Select from TorGuard server list
- Username: Your VPN account username
- Password: Your VPN password
- Authentication: MS-CHAPv2
- Encryption: Medium (AES40/128 bit)
- Use default gateway on remote network: ✓ Activated
- Allow other network devices to connect: Enable for VPN sharing
- Reconnect when VPN connection is lost: ✓ Activated
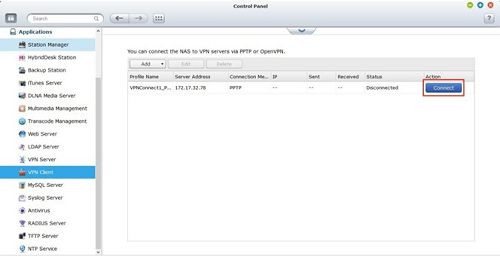
Step 4: Connect to VPN
Click the blue Connect button next to your profile:
Verify VPN Connection
Method 1: SSH Command
Login to NAS via SSH and run:
curl http://checkip.dyndns.orgMethod 2: Web Interface
- Check connection status in VPN Client panel
- Look for green "Connected" status
- Verify assigned VPN IP address
Method 3: Container Station
# If using Docker/Container Station
docker run --rm curlimages/curl http://ipinfo.ioAdvanced VPN Configuration
VPN Gateway for Network
Share VPN connection with entire network:
- Enable "Allow other network devices to connect"
- Configure DHCP to use NAS as gateway:
- Router DHCP: Set NAS IP as default gateway
- Or manually configure devices
Split Tunneling
Route only specific traffic through VPN:
# Add to OpenVPN config
route-nopull
route 10.0.0.0 255.0.0.0 vpn_gatewayKill Switch Implementation
#!/bin/bash
# QNAP VPN kill switch script
iptables -I FORWARD -i eth0 -o tun0 -j ACCEPT
iptables -I FORWARD -i tun0 -o eth0 -j ACCEPT
iptables -I FORWARD -j DROPNAS VPN Performance Tips
- CPU Considerations:
- VPN uses significant CPU resources
- Monitor with Resource Monitor
- Consider hardware upgrade for high speeds
- Protocol Selection:
- WireGuard: Best performance/security ratio
- OpenVPN UDP: Better than TCP
- Avoid PPTP/L2TP for security
- Buffer Tuning:
# Add to OpenVPN config sndbuf 524288 rcvbuf 524288 push "sndbuf 524288" push "rcvbuf 524288"
QNAP VPN Use Cases
| Use Case | Configuration | Benefits |
|---|---|---|
| Remote Access | Standard VPN client | Access files securely |
| Download Station | VPN + Download apps | Anonymous downloads |
| Network Gateway | VPN sharing enabled | Whole network protection |
| Docker Apps | Container routing | App-specific VPN |
Docker/Container VPN Setup
For container-specific VPN:
# Docker compose example
version: '3'
services:
vpn:
image: qmcgaw/gluetun
cap_add:
- NET_ADMIN
environment:
- VPN_SERVICE_PROVIDER=custom
- VPN_TYPE=openvpn
- OPENVPN_CUSTOM_CONFIG=/config/torguard.ovpn
volumes:
- ./config:/config
ports:
- 8888:8888/tcp # HTTP proxy
app:
image: your-app
network_mode: service:vpn
depends_on:
- vpnTroubleshooting VPN Issues
Connection Failures
- Wrong credentials: Check VPN username (not email)
- Server down: Try alternate server
- Port blocked: Try different protocol/port
- Firmware: Update QTS to latest version
Slow Speeds
- Check CPU usage during transfer
- Try different VPN protocol
- Select closer server location
- Disable unnecessary QNAP services
DNS Leaks
- Configure DNS in VPN settings
- Add to config:
dhcp-option DNS 1.1.1.1 - Test at dnsleaktest.com
Security Best Practices
- Never use PPTP for sensitive data
- Enable 2FA on QNAP admin account
- Firewall rules: Restrict NAS access to VPN only
- Regular updates: Keep QTS and apps updated
- Backup VPN configs: Store securely off-NAS
- Monitor logs: Check for unauthorized access
💡 Pro Tip: WireGuard on QNAP
For best performance and security:
- Install WireGuard from QNAP Club repository
- Use TorGuard's WireGuard config generator
- Enjoy 5x faster speeds than OpenVPN
Need QNAP VPN Help?
Our support team can assist with QNAP-specific VPN configuration, performance optimization, and troubleshooting connection issues.
Get NAS Support